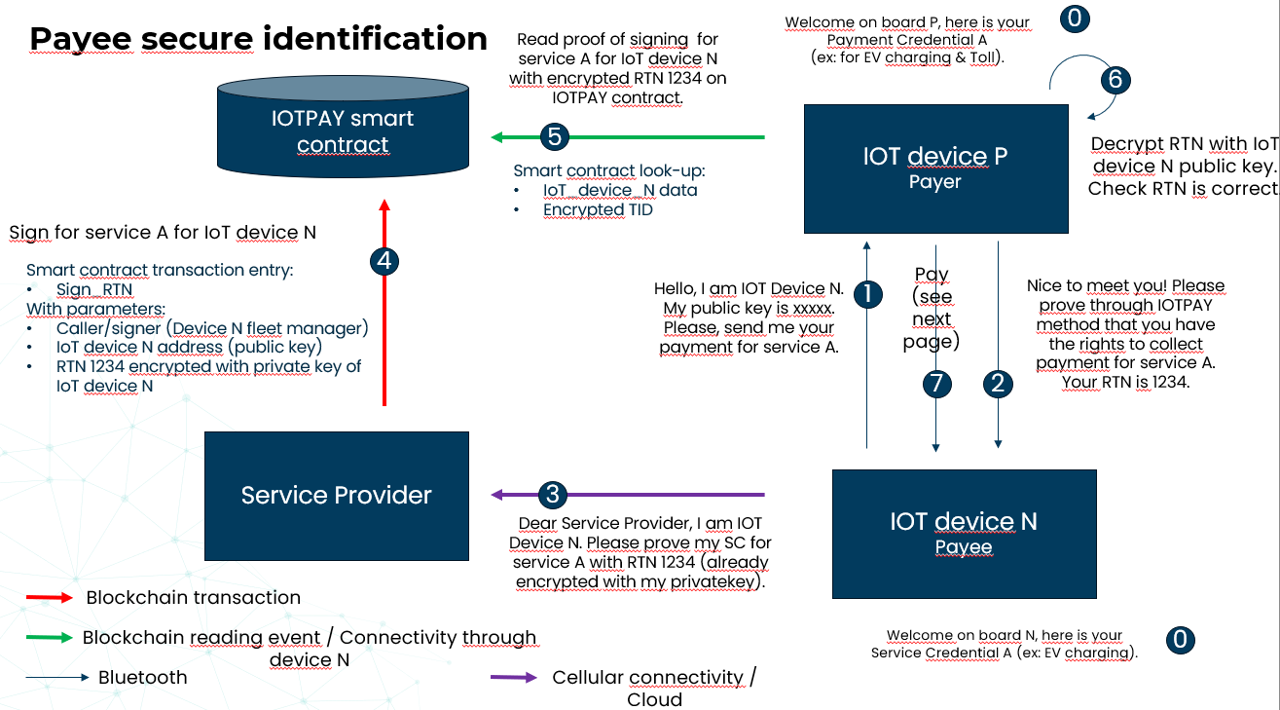
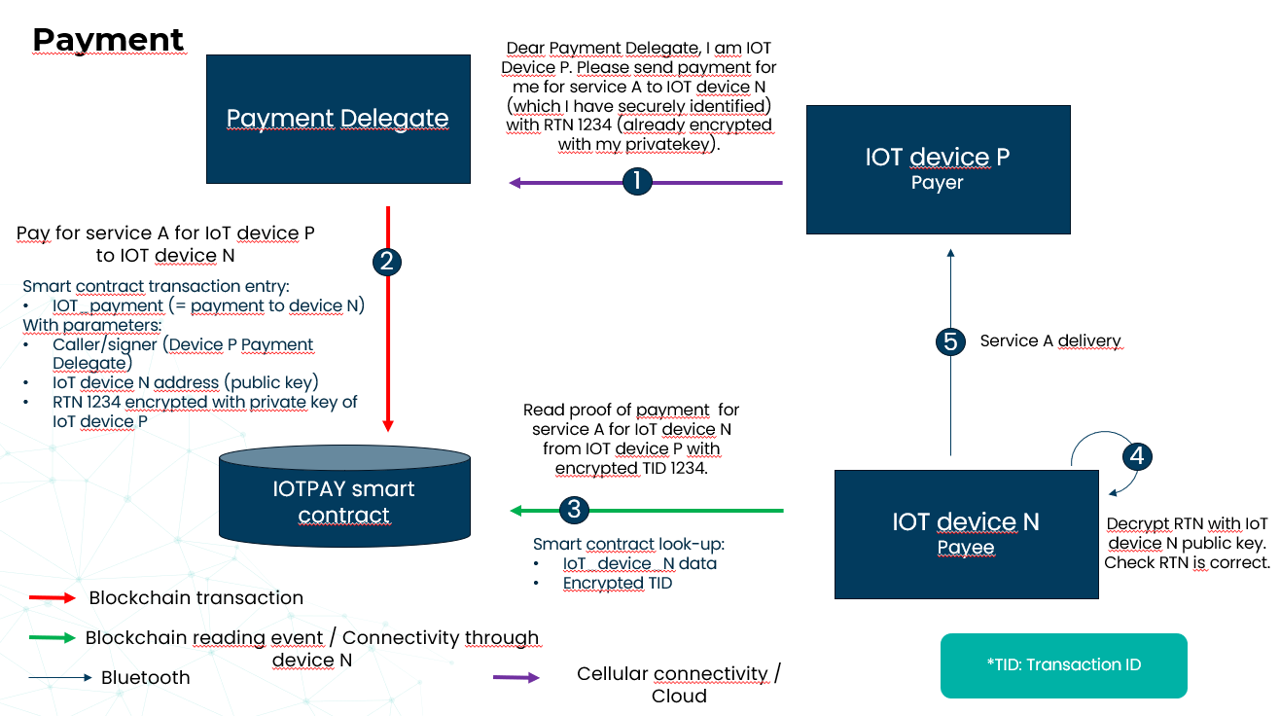
Today the Internet of Things, or IoT, is increasingly a part of everyday life, from smart homes to complex industrial systems. Almost half of the 160 ZBs (zettabytes) currently produced in the world are generated by IoT devices. Although it is difficult to determine the exact market size due to different segments and applications, several market research companies have estimated the size of the Big Data market.
According to various market research reports which were made between 2020 and 2021, the Big Data market was valued between US $138.9 billion and US $156 billion and is expected to grow at a significant CAGR (compound annual growth rate) in the coming years. The reports highlight the growing penetration of mobile devices and the growing need for simplified data sharing processes as key drivers for the growth of the market research market. The IoT automated data exchange market is also a rapidly growing industry with significant future growth potential, consistent with this general trend.
Unfortunately, as the number of devices in the system rises, so does the demand for data sharing that is dependable and effective as well as for their protection. As of right now, centralized institutions like banks, governments, and social media companies are in charge of maintaining our online identities. This method is not appropriate for Internet of Things (IoT) devices, which can, and in some cases should, be autonomous, with limited memory or processing power, and operate in unreliable environments.
Now we can address these issues by utilizing smart contracts and blockchain technology. Blockchain is a viable foundation for developing secure Internet of Things systems because of its decentralized and immutable nature, which provides high levels of security and transparency.
Obviously, building a decentralized public key infrastructure framework for connected devices allows for removing all centralized bodies from the ecosystem of many businesses. Therefore, this brings back each final user as the focus of the technical architecture of services offered by these connected devices.
Indeed, this prioritizes the assessment of data trustworthiness, the interoperability and sustainability of the digital identity, and data minimization (a requirement of GDPR).
In our concept we envision a cutting-edge method for authenticating devices in an IoT network by using the capabilities of smart contracts. And our objective is to develop a platform that offers device authentication and service management, facilitating secure and productive user interaction within the IoT ecosystem.
Our method tackles several important IoT security issues:
1) Device Authentication: The assurance of device authentication removes the potential for identity spoofing.
2) Data Verification: Ensures the validity of data originating from devices, which is especially important for critical applications.
3) Service Management: Creates a flexible and scalable system for managing device and service interactions.
Our solution’s goal is to enhance trust in IoT systems while enhancing its functionality and security. It creates new opportunities for the creation and implementation of intelligent services, which have the potential to transform various aspects of our lives and jobs.
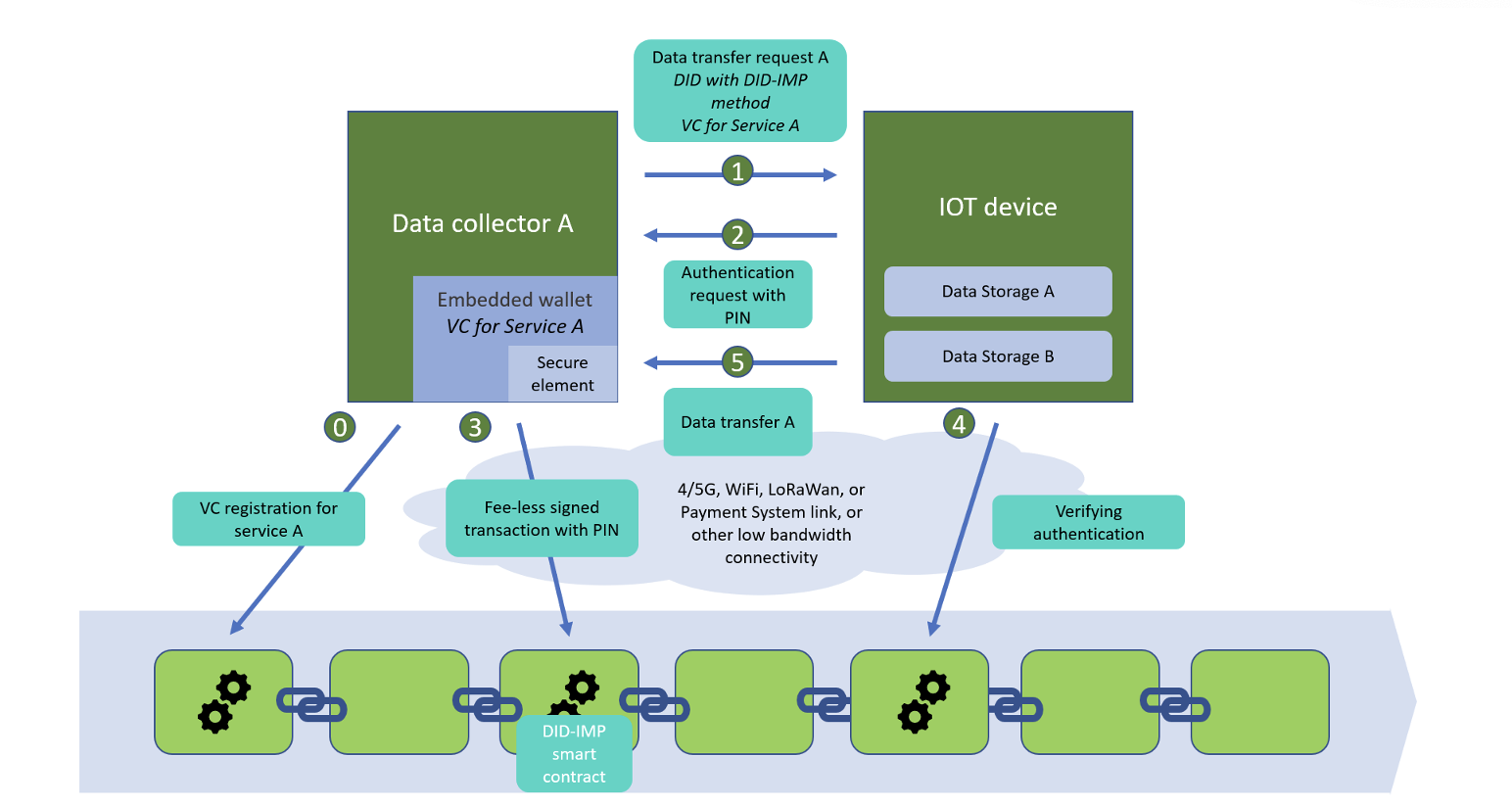
A. An overview of the core components
DID-IMP‘s decentralized public key infrastructure is meant to allow any connected object to be able to automatically identify and proceed with secure data sharing or procuring. We will develop the key software components to deliver a fully functional product (pic. 1), at Technology Readiness Level 7 or 8. To achieve this, the proposed architecture will rely on:
1) A public blockchain network: the layer 1 blockchain network will be chosen in accordance with TRUSTCHAIN strategic orientation, taking into account the need for an EVM for ease of implementation. The cost performance (gas fee) of the chosen network will be very important to ensure the economical sustainability of the solution.
2) A set of smart contracts: these smart contracts will be used to issue and revoke certificates. They will also allow to automate fee-less data sharing processing and enforce data sharing conditions. For realizations fee-less transactions:
We will use the possibilities of Alastria as a public-permissioned blockchain to transfer-data in a fee-less way.
In order to expand our solution’s capabilities, including the potential use of other blockchains every function in our smart-contracts will have a signature parameter. Devices which want to interact with smart-contracts must sign the function parameters with their account’s private key and send it to the smart contract owner (via any communication channel). The owner then submits the parameters along with the signature to the blockchain, paying for gas. The signature guarantees that the message was approved by the user.
3) An embedded wallet: this software will be designed to be usable in the connected objects. It will be used to manage digital currency and tokens associated with the blockchain IoT data sharing solution or loads of data. This software can be used to store, send, and receive data, depending on the configuration. The part of managing the DIDs and VCs could be implemented by relying on the Veramo project. It is an open-source project, providing us with the opportunity to either use it as a starting point and implement it into our product or modify it to align with our goals, leveraging it as a foundation.
4) User interface: this is a web application for IoT Services Providers which will be used to activate and revoke certificates. This tool is intended to be the visual interface allowing to manage and trace data and object certificates and also fraud detection, and dispute resolution.
5) A mobile application version of the user interface with a selected number of key administration features.
B. Principle of operation
1) Registration and service creation:
- Users register their devices by creating DIDs and associating them with other addresses.
- Any user with a DID can create a ”service” (e.g. ”Temperature data in different rooms of the house”) and become its owner.
- VC owners can join the service via a smart contract, forming a fleet of devices working together.
2) Data exchange between IoT devices:
Each IoT device has a built-in blockchain wallet for signing data. Two devices exchange DID and VC to communicate.
The sending device verifies the information of the receiving device.
On successful verification, the sending device generates a pin code and sends it to the receiving device.
The receiving device signs the pincode by executing a transaction on the blockchain.
The sending device verifies the transaction and, if correct, sends the data.
Overall, our blockchain-based solution requires a range of software components that work together to provide secure, decentralized data sharing or data sharing processing for connected devices and services. These components will be designed to ensure high levels of security, efficiency, and usability.
Decentralization: True to the concept of DIDs, the solution will operate in a decentralized manner, avoiding single points of failure and ensuring that no central authority can compromise the integrity of the network nor has an unbalanced predominant role.
Scalability: Given the potential vast number of devices in IoT, the solution will be able to handle a large and rapidly growing number of identifiers and a very large amount of data transfers.
Feeless: A good DID solution should be efficient in terms of blockchain gas consumption so we will create it in fee-less way for users.
Maturity: We have communicated with potential clients, so we are developping solution based on their needs.
Ease of use (App): We expect to create a user-friendly application that does not require the end user to spend time understanding how to manage their devices.
Reliable identification of devices: The project will demonstrate high reliability in identifying IoT devices with unique DIDs and VCs verified via blockchain, which provide a high level of security and trust that is critical for IoT ecosystems.
In this part we would like to describe specific real-world scenarios where our design could be used.
A. Connected cars
With DID-IMP, vehicles would be able to automatically transmit data about parking, charging and other transport processes, making the services more comfortable for drivers. They will be able to send maintenance data using IoT data transfer between devices within their respective organizations' fleets.
In the simplest case, the station system communicates with the vehicle, authenticating it and its owner using DID-IMP for secure data exchange. The refueling hose with IoT sensors automatically connects to the vehicle’s fuel tank, initiating the refueling process and monitoring pressure and temperature to optimize safety. Once the refueling is complete, a digital receipt is sent to the driver’s smartphone, where transaction history and fuel efficiency metrics can also be viewed.
B. Remote healthcare
DID-IMP would be able to improves access to telemedicine and remote patient monitoring while ensuring data security and personalization. For example, a user has different IoT health monitoring devices like fitness trackers, smart scales, tonometers etc. And user’s phone collect data from then via the DID-IMP app and synchronize it with an electronic medical record. Using this data the medical app can provide personalized recommendations and notifications of potential health issues or even notify emergency services and the user’s contacts in emergency situations.
C. Cognitive cities
DID-IMP would be able to enables secure data exchange between IoT devices, helping to create smart/cognitive cities. Users register their devices through the DID-IMP app, linking them to decentralized identifiers (DIDs) and verification certificates (VCs).
Once registered, users could customize program settings according to personal preferences by selecting devices to communicate with, configuring data sharing settings, and receiving real-time notifications. With DID-IMP, users can easily connect to city IoT devices to monitor traffic, control water usage, manage waste and receive safety notifications. Devices exchange data through smart contracts, ensuring that information is verified and protected.
DID-IMP protects personal data, contributes to the city’s sustainable development goals and provides users with access to a variety of innovative services, making their lives more convenient and safe.
D. Energy Managment
DID-IMP enables secure management of IoT devices in the energy industry, such as smart meters and grid sensors. Users register devices through the DID-IMP app, enabling accurate and secure data exchange.
The app provides real-time data on energy consumption and distribution, allowing users to monitor trends and receive alerts when problems occur. Users can participate in local energy communities, sharing data to optimize energy use and deploy renewable sources.
DID-IMP makes it easy to register and manage IoT devices, monitor energy and participate in energy communities through secure data sharing.
E. Smart Homes
DID-IMP would be able to enable secure control of smart home IoT devices such as thermostats, cameras etc. Users download the DID-IMP app and go through a simple setup process, registering each device and associating it with the DID.
The DID-IMP app would allow for real-time monitoring, sending notifications about events such as movement in front of the camera or temperature changes. This enables to monitor the safety, energy consumption and condition of the house.
Of course, data privacy and security are paramount when it comes to such a private aspect of life as our homes. DID-IMP would use authentication mechanisms to protect against unauthorized access.
F. Supply Chain
DID-IMP provides an opportunity to leverage IoT technologies for logistics and supply chain management, enabling secure data exchange to monitor the location, condition and status of shipments during transportation to help prevent theft, damage or tampering.
For example, a logistics company specializing in the transportation of perishable goods can use DID-IMP to integrate IoT devices such as temperature sensors and GPS trackers. Once successfully integrated, the company has access to a dashboard that displays realtime location and temperature information for each device. Automatic notifications of any deviations or unexpected events help to take instant action to prevent spoilage of goods. In addition, the application allows you to analyze historical data, identify trends and optimize delivery processes. Effective integration with other company systems improves visibility and transparency in the supply chain, facilitating better collaboration between process participants.
In this chapter, we provide a concise overview of the fundamental structural features of implementing smart contracts, as they form the core of the project.
The system consists of seven smart contracts:
1) DidBase - basic functions for managing DID (all implemented to be called only from the inheriting contract);
2) VCBase - basic functions for managing VC (all implemented to be called only from the inheriting contract);
3) CheckSignature - signature verification function;
4) DelegateTypes - definition of the basic structure of VC and
hashing;
5) Constants - a set of constants of type bytes32 used in data
signing;
6) DIDRegistry - calls functions from DidBase, where for each function from DidBase there are two corresponding functions - one can be called directly by DID address, the other accepts signed data and can be called by an address not related to DID;
7) VCRegistry - calls functions from DidBase, where for each function from DidBase there are two corresponding functions - one can be called directly by DID address, the other accepts signed data and can be called by an address not related to DID.
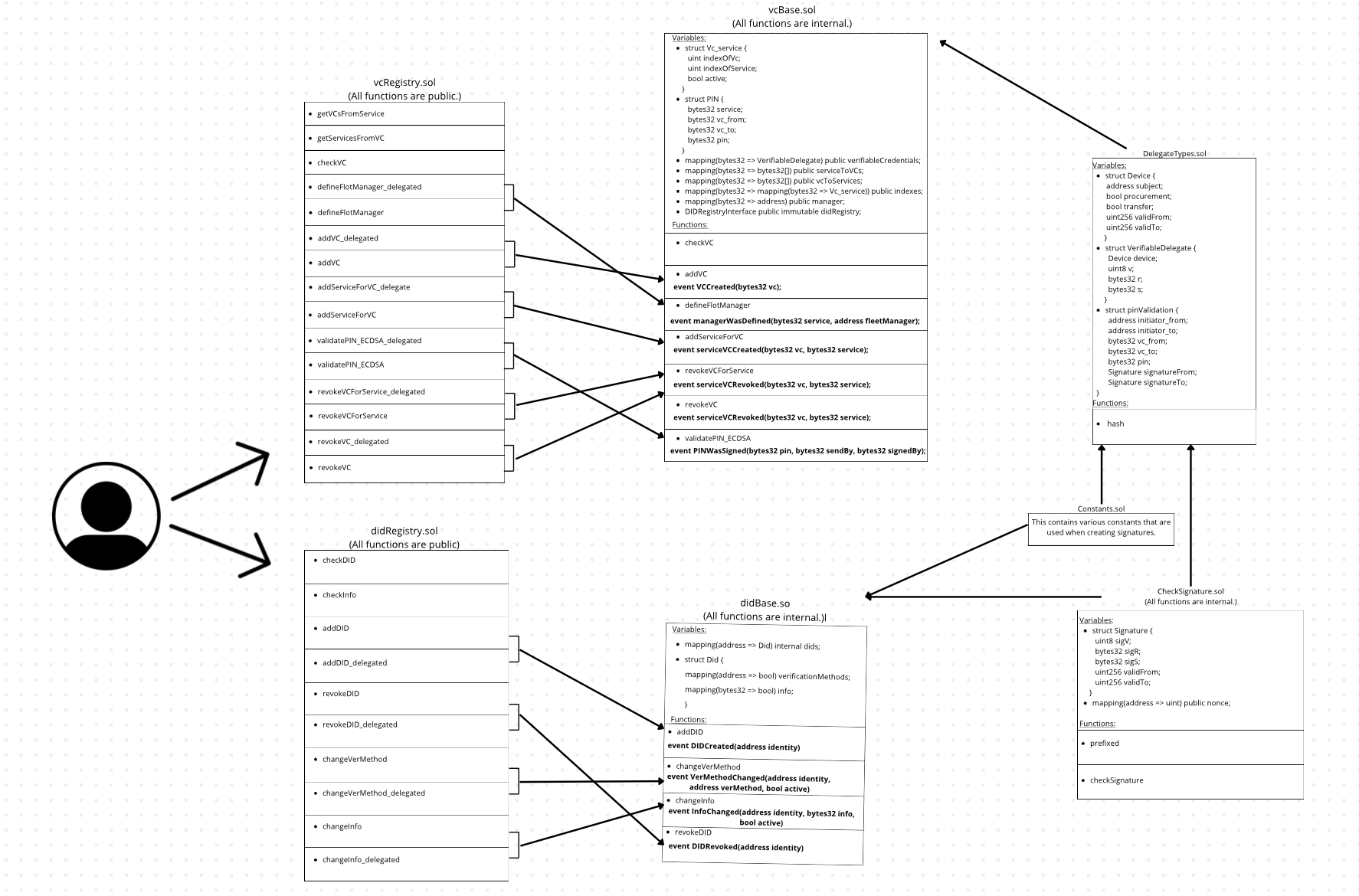
In conclusion, we believe that this project is a step towards improving data security and efficiency in various areas through the use of decentralized identifiers (DIDs) and verifiable credentials (VC). By introducing smart contracts as the basis of the system, we can create a reliable basis for secure data exchange and verification.
After completing the development of the main details of the application, we consider the next steps in the development of the idea and project:
Implementing NFT (Non-Fungible Tokens) technology to create tokenization in the data transfer process, which will improve the transparency and efficiency of the system. It will also help project integrate more easily into areas where you need to pay for data.
Exploring and enabling different methods of data transfer, including using transactions not only for verification but also for storing the sent data, which will further enhance the security and reliability of the system. This will give us different levels of security and privacy that can be set by users according to their needs.
Implementing zero-knowledge proof technologies to maximize data protection and anonymity, making the system even more secure and attractive to users. These steps will help improve our project and expand its capabilities, making it even more useful and promising in the digital sphere.